User Behavior Analytics, a powerful tool in cybersecurity, delves into the depths of user actions to detect threats and enhance network security. From insider threats to fraud detection, this topic unravels the secrets behind analyzing user behavior.
Exploring the concept, implementation, benefits, and real-world examples, User Behavior Analytics opens a door to a world where data tells a compelling story of security and risk management.
Overview of User Behavior Analytics
User Behavior Analytics (UBA) is a cybersecurity process that focuses on detecting and identifying abnormal user activities within a network. By analyzing patterns of behavior, UBA helps organizations identify potential security threats and insider risks.
How User Behavior Analytics Works
User Behavior Analytics typically involves collecting and analyzing data from various sources such as network traffic, logs, and endpoint devices. By using machine learning algorithms and statistical analysis, UBA tools can establish a baseline of normal behavior for each user and detect deviations from this baseline.
Benefits of User Behavior Analytics
- Early Detection: UBA can identify potential security incidents before they escalate, allowing organizations to respond quickly.
- Insider Threat Detection: UBA can detect unusual behavior patterns that may indicate insider threats or compromised accounts.
- Reduced False Positives: By focusing on user activities, UBA can reduce the number of false positive alerts generated by traditional security systems.
Examples of User Behavior Analytics Tools
Splunk: Splunk offers a UBA solution that can analyze user activities in real-time to detect anomalies and potential threats.
Darktrace: Darktrace uses AI algorithms to monitor user behavior and detect suspicious activities within a network.
Exabeam: Exabeam provides a UBA platform that combines machine learning and data analytics to identify security incidents based on user behavior.
Importance of User Behavior Analytics
User Behavior Analytics (UBA) plays a crucial role in enhancing cybersecurity measures by detecting insider threats, improving network security, and aiding in fraud detection.
Detecting Insider Threats
User Behavior Analytics is essential for identifying suspicious activities within an organization that may indicate insider threats. By analyzing user behavior patterns, UBA can detect anomalies and unusual actions that might go unnoticed through traditional security measures.
Improving Network Security
User Behavior Analytics helps in enhancing network security by monitoring user activities, detecting unauthorized access, and identifying potential security risks. This proactive approach allows organizations to respond quickly to any security incidents and prevent data breaches.
Role in Fraud Detection
User Behavior Analytics is instrumental in fraud detection by analyzing user actions and identifying fraudulent behavior. By establishing baseline behavior and flagging deviations, UBA can help in detecting fraudulent activities such as identity theft, financial fraud, and other malicious behaviors.
Implementation of User Behavior Analytics
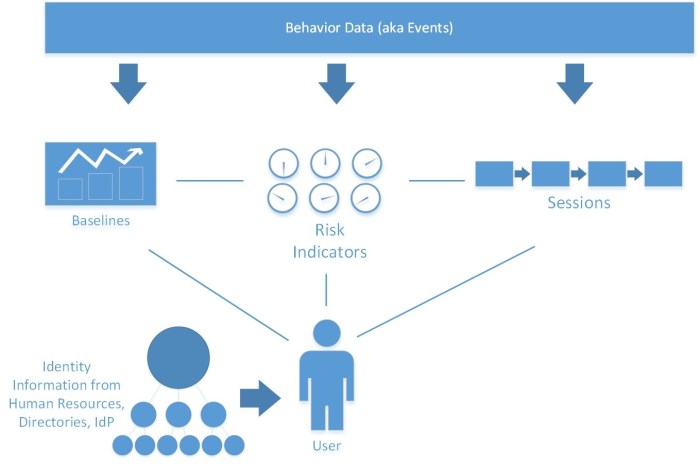
When it comes to implementing user behavior analytics in an organization, there are several key steps involved in order to effectively track and analyze user actions to improve business outcomes.
Step 1: Define Goals and Objectives
To kick things off, it’s crucial to clearly define the goals and objectives of implementing user behavior analytics. This involves identifying what specific metrics and KPIs the organization wants to track and improve upon.
Step 2: Choose the Right Tools, User Behavior Analytics
Next up, selecting the appropriate user behavior analytics tools is essential. There are various platforms available in the market, each with its own unique features and capabilities. It’s important to choose a tool that aligns with the organization’s goals and budget.
Step 3: Collect and Analyze Data
Once the tools are in place, the organization needs to start collecting and analyzing user data. This includes tracking user interactions across various touchpoints, such as websites, mobile apps, and social media platforms.
Step 4: Interpret Data and Draw Insights
After collecting the data, it’s time to interpret the findings and draw actionable insights. This involves identifying patterns, trends, and anomalies in user behavior that can help the organization make informed decisions to enhance user experience and drive business growth.
Step 5: Implement Changes and Monitor Results
Finally, the organization should implement changes based on the insights gained from user behavior analytics and continuously monitor the results. This iterative process allows for ongoing optimization and improvement of user experience.
By following these steps, organizations can successfully implement user behavior analytics to gain valuable insights into user actions and preferences, ultimately leading to better decision-making and enhanced business performance.
Benefits of User Behavior Analytics
User Behavior Analytics (UBA) offers several advantages in the realm of threat detection and incident response. By analyzing user actions and behaviors, organizations can proactively identify potential security threats, mitigate risks, and enhance their overall cybersecurity posture.
Enhanced Threat Detection Capabilities
User Behavior Analytics enables organizations to detect abnormal or suspicious activities that may indicate a potential security breach. By establishing baseline behavior patterns for users, UBA solutions can quickly identify deviations from the norm, such as unauthorized access attempts, unusual login times, or unusual file access patterns. This proactive approach allows security teams to respond swiftly to potential threats before they escalate, reducing the impact of cyberattacks.
Improved Incident Response
Incorporating User Behavior Analytics into incident response strategies enhances the effectiveness and efficiency of security teams. By providing real-time insights into user activities, UBA solutions enable rapid detection, investigation, and remediation of security incidents. By correlating user behavior data with threat intelligence feeds, security analysts can prioritize alerts, streamline incident response workflows, and allocate resources more effectively.
Real-World Case Studies
Several organizations have successfully leveraged User Behavior Analytics to strengthen their cybersecurity defenses and protect sensitive data. For example, a financial services company detected a sophisticated insider threat using UBA, uncovering unauthorized data exfiltration attempts by a disgruntled employee. By promptly identifying the anomalous behavior, the organization was able to prevent a data breach and mitigate potential financial losses. Similarly, a healthcare provider utilized UBA to detect and thwart a ransomware attack that targeted vulnerable endpoints within their network, safeguarding patient information and maintaining operational resilience.
